May 25, 2017
The insurance industry has been in the spotlight following the recent global ransomware attack, WannaCry – potentially the world’s largest cyber-event to date. While governments and cybersecurity experts attempt to trace the culprit, companies around the world are beginning to explore the idea of cyber coverage to transfer some of the potential risks of a cyber-event. The Council’s biannual Cyber Market Watch Survey found risk transfer as the number one driver for the purchase of cyber coverage among small businesses and large entities.
Although 74 percent of cyber polices cover cyber extortion costs, the 300,000 affected computers from WannaCry exist mostly outside the United States, which accounts for 90 percent of the world’s cyber polices. As a result, cyber insurance will cover just a small fraction of overall losses from WannaCry but the event’s publicity has emphasized the need for comprehensive and affordable cyber insurance coverage across the globe.
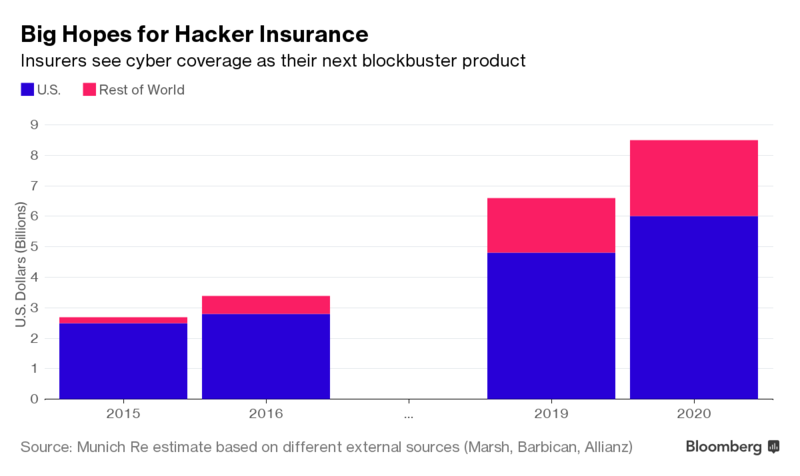
But the attack has not all been bad news, at least not for the insurance industry. The ransomware attacks have served as free advertising to put in place cyber coverage. The insurance industry has experienced a steady up-tick in take-up rates. Munich Re’s latest projection expects the industry to write as much as $10 billion of cyber insurance premiums by 2020, up from $3.4 billion currently.
So, what does this mean for the insurance industry? Certainly, an increased interest in cyber coverage in the U.S., but particularly in Europe and Asia. Driven by regulation and the legal environment, the U.S. is by far the biggest purchaser of cyber insurance but Tom Reagan, Marsh’s cyber practice leader, explained that the attack will lead to more companies outside the U.S. buying cyber coverage. “We’ve already started getting the phone calls,” said Reagan, but the international take-up rate for cyber remains extremely low.
According to The Council’s Cyber Market Watch Survey, roughly 32 percent of U.S. respondents’ clients purchased cyber insurance in the last six months. However, while cyber insurance take-up is on the rise, organizations of all sizes are still not doing enough from a cybersecurity standpoint. Only 31 percent of respondents’ clients have a proactive information program in place with capabilities in prevention, detection, containment and response/eradication. In order to mitigate the risk of an aggregate attack, the insurance industry will have to broaden and deepen its cyber risk management role through more technical expertise and alliances with cybersecurity vendors.
This event illustrates the importance to evaluate what is and is not covered in a cyber policy. While coverage for extortion, business interruption and costs from outside experts is often included under cyber policies that many organizations buy, Brian Dusek, attorney at McCullough Campbell & Lane L.L.P explains, “there’s often language in the policies saying that the policyholder has to keep reasonable security practices in place, and the patch has been out since March,” which could result in voided policies if organizations failed to keep their systems up-to-date.
WannaCry has also brought to life a concerning challenge for the insurance industry – aggregate risk. Not only could a ransomware attack trigger claims across policies beyond cyber extortion, including incident response, business interruption, data and software loss, and even kidnap and ransom (K&R) policies, but the possibility of an aggregate attack extends beyond geographic location or industry, and could lead to massive losses from multiple policyholders.
Fitch Ratings explains that insurers should approach cyber coverage cautiously, as pricing uncertainty and a lack of actuarial data for underwriting purposes could lead to industry-wide losses and negative credit ratings. When assessing potential losses, insurers need to “stress-test” their cyber exposures against both singular events and aggregation scenarios.


