September 11, 2018
This month, The Council compared five recent major regulatory changes in the cyber security space:
- EU’s landmark General Data Protection Regulation (GDPR);
- the New York Department of Financial Services Cybersecurity Rule (23 NYCRR 500);
- the California Consumer Privacy Act of 2018 (CCPA);
- the Protections For Consumer Data Privacy bill, recently passed by Colorado (HB18-1228); and
- the NAIC Insurance Data Security Model Law (NAIC Model Law), which to date has been adopted only by South Carolina.
Several questions are of obvious concern to the industry, but perhaps the most important is, “How similar are these new laws to the GDPR?”
The GDPR’s reputation suggests it may be the most extensive of the five new laws, and for the most part, this is true. There are, however, a few areas where U.S. regulations take things a step further than the GDPR. Consider the following chart (click here for PDF with definitions of rights):
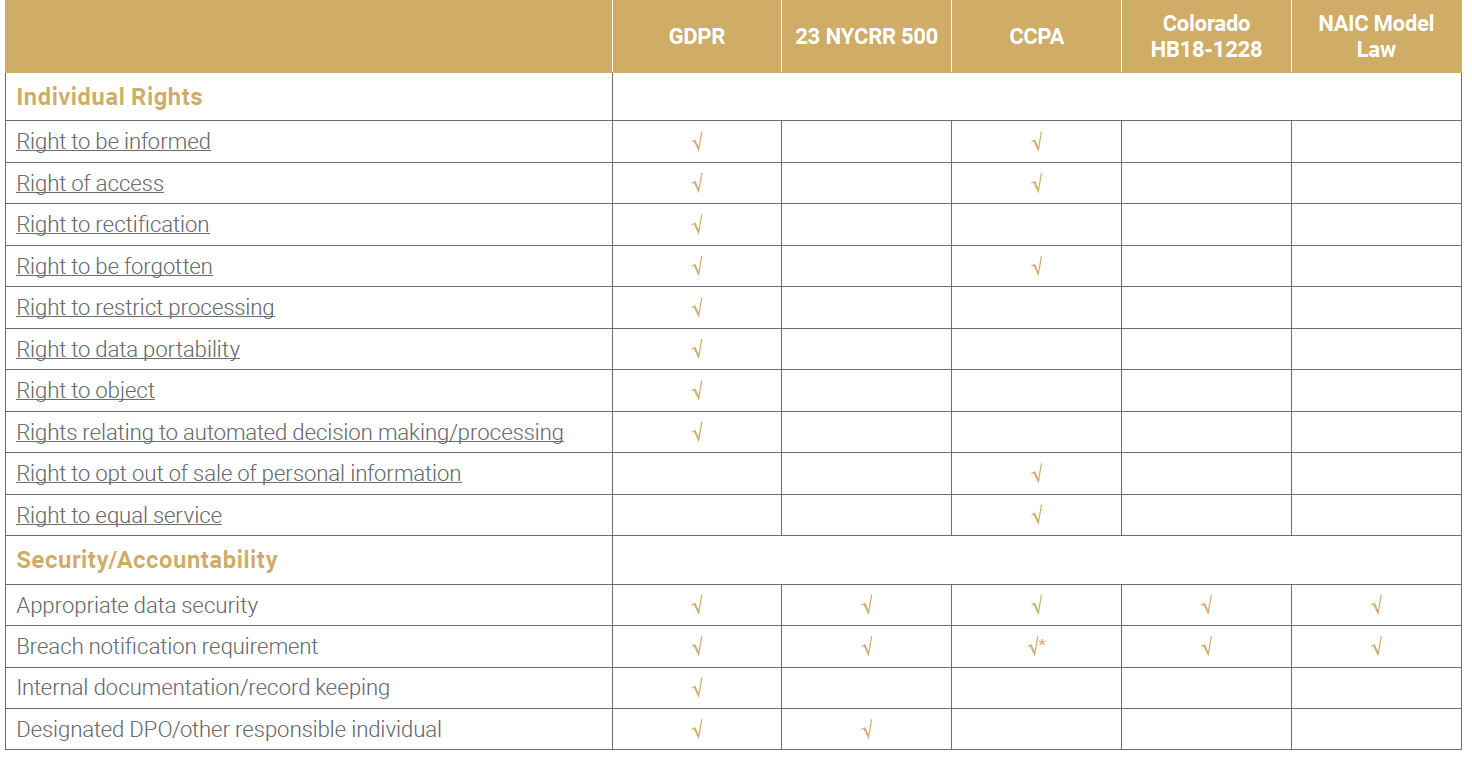
Notably, of the four laws, only the GDPR and the CCPA explicitly enumerate individual rights of the consumer. New regulations coming from U.S. states seem to focus mainly, if not exclusively, on the security and accountability aspects of consumer data privacy. As seen in the table, all U.S. regulations require companies to implement appropriate data security measures to protect the consumer data they hold, and both either impose a breach notification requirement (23 NYCRR 500, HB18-1228, NAIC Model Law) or strengthen it (CCPA by allowing for suing over breach notification violations). However, only 23 NYCRR 500 and the NAIC Model Law have a breach notification timeframe as demanding as the GDPR, dictating that notification must be made 72 hours after a breach has been discovered.
On the other hand, in the realm of security and accountability, 23 NYCRR 500 (as well as the NAIC Model Law, which closely follows it) is, in one aspect, more extensive than the GDPR. For example, though the GDPR requires “appropriate data security,” it provides no definition or checklist, whereas 23 NYCRR 500 lays out several explicit steps companies are required to take for data security purposes. Section 500.05 obligates companies to perform annual penetration testing of their systems and biannual vulnerability assessments, and §500.12 outlines access requirements for a company’s system: multi-factor authentication or “reasonably equivalent” access controls.
Of course, this comparison is not to imply that compliance with any of the regulations will be somehow “easier” than compliance with any of the other ones; all five new regulatory packages impose requirements that businesses will have to work hard to follow. But more awareness of the similarities and differences between all five laws could hopefully help businesses better orient their ongoing compliance efforts.


